When Anonabox appeared on the crowd funding scene last month, a lot of information security professionals and privacy advocates were rightly annoyed by the dishonest claims made by the creators. Many of us spent quite a while raising questions and promoting concerns on various forms of media, until thankfully Kickstarter suspended the project. We don’t actually know what the final trigger was, but we do know that a concerted effort by a focused group can stop crowd funding projects in their tracks.
Since Anonabox, many more privacy projects have appeared. There are Tor routers that don’t make outlandish claims. There is Anonabox on Indiegogo. There is also Wemagin.
Wemagin has a glossy website, professional videos, very bold claims, and some very vehement (but also, incredibly stupid) supporters.
Initial concerns
Wemagin make some bold, very assertive claims that set my alarm bells ringing:
- No trace is left on the computer that the device is used on
- No trace is left on the Internet when you use the device (including when accessing your banking website)
- It can run on any computer/it requires nothing from the computer to operate/can be used with public PC
- It can be used inside countries like North Korea safely
Why are these so worrying? Because there is no way that they are true.
1. No trace is left on the computer that the device is used on
This simply isn’t possible with modern operating systems.
The second you insert a USB device into a normal Windows machine, it leaves a plethora of traces. Some are very obvious (openly in the registry), others not so obvious, and some can only be recovered using advanced forensic techniques. This would at least prove you had used the Wemagin device.
Run an executable, startup a VM or create a new network interface and you leave even more trace behind. Wemagin is going to have to do one or more of these to work.
One supporter said “you can run things from the PC ram alone alone”. This really isn’t true anymore with an application of any size. Even if it was, the second a laptop or desktop hibernates, it writes the RAM to disk. This can then be forensically analysed – leaving a trace. It is very difficult to prevent or remedy this.
Wemagin could say that they leave “little trace”, but they don’t – they say “no trace”.
2. No trace is left on the Internet when you use the device (including when accessing your banking website)
Wemagin seems to be a VPN and browser package. A VPN will make it appear as if you are using the Internet from another IP address.
If you visit a website, the website logs will still have a record of your visit, albeit with a different IP to the IP of the PC you are using. This is not “no trace”.
Login to a website, and there will be a record of that login happening. This is not “no trace”
Your ISP is also capable of logging your connection to Wemagin’s VPN servers. They wouldn’t be able to observe the traffic, but they would know you had established a VPN connection.
Tracking cookies and other techniques (such as browser fingerprinting) mean that you can be tracked across multiple sites. Log into one site and you can be tracked to others even if using a VPN.
Using a VPN leaves less trace (or, at least, a more convoluted one), but calling it “no trace” is not true.
3. It can run on any computer/it requires nothing from the computer to operate/can be used with public PC
Setting up a VPN and running a browser from a USB memory device isn’t a trivial action on a PC. You will need to be able to access the USB port, the system will have to mount the USB device, be able to run executables from the USB device, establish a network connection to a given IP and port, possibly create a new network adapter. Often one or more of these will be disallowed on a public PC.
Our local library PCs run Symantec Endpoint, preventing USB sticks from being used without a password, and even then, no executables are allowed. There are other serious restrictions in what can be done – only a few select applications can be run. Web access is via a locked down proxy that cannot be reconfigured. This is fairly common on public PCs I have seen in airports, hotels, and schools.
It is also perfectly possible for firewall and filters to detect VPN usage even on non-standard ports. The traffic is encrypted but it isn’t magically disguised. Many corporate environments will flag and alert techniques used to evade filters.
Wemagin might have been doing something clever to get around these issues, but the creator has confirmed that they aren’t.
4. It can be used inside countries like North Korea safely
The Wemagin video shows emaciated North Korean children and talks of death penalties. They very strongly imply that using the Wemagin device in North Korea is safe.
Mainstream VPNs are not adequately safe for all purposes inside of North Korea or China without following a lot of OPSEC rules and being very careful.
VPNs alone are not enough to protect your privacy if your adversary is a nation state – especially if you are claiming that it is so easy to use that your grandmother can use it.
Further issues
Those 4 issues were the ones that made me concerned. Looking deeper though, there are many, many more issues:
5. With a VPN you are reliant on trusting the VPN provider to stay anonymous
A VPN server – especially one that is a paid for service – has to have at least some notion of who is using it and what they are doing. This in turn means you are reliant on the VPN provider holding no logs and not co-operating with law enforcement/government.
This is a dangerous position to be in if you are relying on the anonymity and privacy of the VPN to keep you safe from harm.
Many European countries and the US have sweeping surveillance rules that can compel ISPs and telecoms providers to wire tap their customers without telling you.
Simple VPNs are fine for people in Western countries who want to bypass web filters or watch Netflix in another region. They are not fine for political activists in repressive regimes.
6. It’s even more complex with a VPN with end-points in multiple countries
There are already countless VPN providers, but they tend to operate their servers in single countries – normally countries that value privacy and have no/low data retention laws.
Wemagin however claims to have VPN end points in 12 countries.
This means that, to keep their users safe, Wemagin need to manage the legal situation in 12 countries.
Steve Kim, the creator has inferred he is not interested in doing this though:
We are dealing with technology capability, not legality disputes.
Again, fine if you just want to watch Netflix in the US from Amsterdam. Not if you are trying to overthrow the government in Iran.
7. The cloud storage is encrypted, but Wemagin also hold the keys
The creator has loosely confirmed that both the customer and Wemagin will hold the encryption keys for the data in the cloud:
Question: [you] will not meet our needs because using the Dropbox model means Wemagin will have access to users’ stored files, and may be able to turn them over to 3rd parties. Will you be offering VPN service without the bundled cloud storage?
Answer: Our cloud is given for free with our VPN. Wemagin has the ability to view. We are not concerned about what you have. At this stage, we need to trust each other.
Wemagin can give the keys to anyone. The keys could be leaked, or obtained by a hacker.
Again, this means that you have to rely solely on trust to protect your data.
Note: This is likely because it is re-labelled cloud storage from another provider.
8. Loads of wishy-washy words and no technical detail.
“Military grade”, “Fast Download Speed” and so on.
There is a total lack of any technical detail on how the system works. For a system that is meant to be shipping in 3 months, this is worrying.
It reminds me of when you ask a kid to invent something: “I invented a spaceship to go to Mars and then we can live on a space base”. The idea is there, but none of the technical know-how.
9. Worldwide patent pending
Another common snake-oil salesman tactic.
There is no worldwide patent system to start with. Patent pending means you have applied for a patent and it has yet to be granted.
But often patents on snake-oil products are on things like cosmetic appearance or other trivialities e.g. the colour and shape of the USB stick, or something totally unrelated to the key selling points like the way a menu can appear or the exact steps needed to login.
This would appear to be the case for Wemagin – the US20130024931 A1 patent largely concerns the UI and usability of a USB stick. It doesn’t even mention VPNs. There’s brief mention of leaving no trace on the host machine:
The operating system operates on the host computer without the host computer being able to detect and store information related to the operation of the flash memory device.
But no description of how this could be achieved.
Rather amusingly, there is an image in the patent like so:
That says quite a lot.
10. Strange wagers to people wanting to test the product
Rather than just… you know… send the product to be tested, you need to go to China and stump up $10k of your own cash.
This seems a fairly common tactic with snake-oil salesmen.
11. Incoherent responses from the creators that fail to address any concerns
Just read the most recent update to backers.
So little of this makes any sense. There is a strong theme of paranoia and also deflection from any of the serious questions.
Steve’s comments aren’t any better. The one where he searches for Rajan’s details, gets them wrong, and then goes on a paranoid rant about competitors is particularly good.
12. An implausibly large team
Really? This many people have worked on a project that has virtually no technical detail? Why are eight law firms involved?
13. The cloud storage appears to be re-labelled livedrive.com
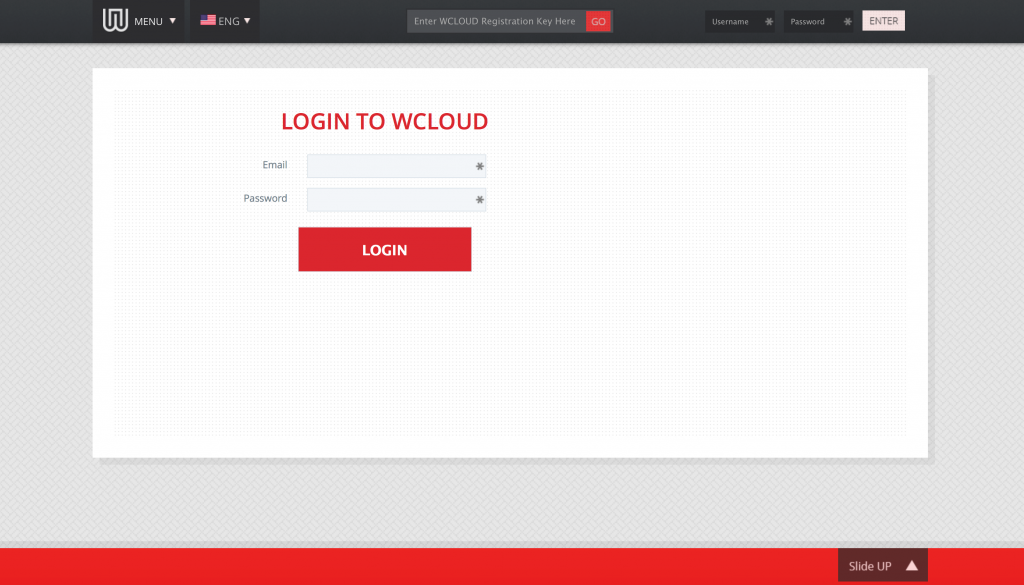
A quick google site search of wemagin.com gets us to a login page for WCLOUD – presumably the cloud storage.
First thing of note – this is not HTTPS. This means that your credentials can be sniffed. There’s not really any excuse for this.
But then, let’s look at the source of the page:
Whilst the form is on the Wemagin site, it is submitting the credentials (in the plain, again) to livedrive.com – an unlimited cloud storage provider.
You pay £39.99 a month to be an unlimited reseller of livedrive.com.
Are they not even planning on keeping this in-house? Livedrive.com has no particular privacy or anonymity focus.
Reselling or using another provider is fine. But you need to be honest about this, especially when you make such bold claims about your product.
14. The VPN appears to be re-labelled IPVanish
The main Wemagin video shows the UI and list of servers used by the VPN.
The UI is virtually identical to the UI of IPVanish. The servers have the same names. IPVanish also have a programme to re-label their product.
Again, re-labelling is fine, but IPVanish is not the VPN solution you need if you are dealing with nation state adversaries.
15. There is an open admin interface on the Wemagin servers
A google site search of Wemagin.com leads to an admin page which has no authentication at all and no encryption.
This page leaks customer details including email addresses and key serial numbers.
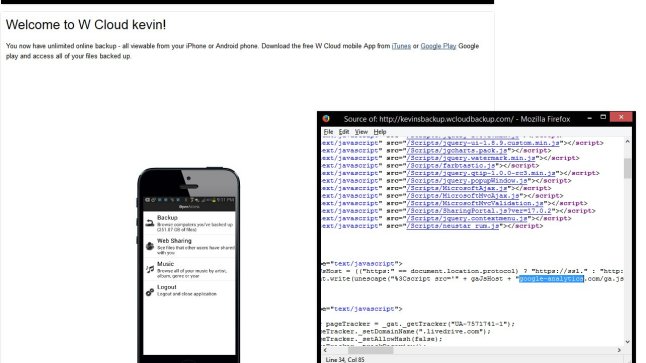
16. The WCLOUD webpages have Google analytics tracking
As someone on 4chan pointed out, the WCLOUD webpages have Google analytics code in them.
This is actively harming your privacy and anonymity.
17. The logins used in the promotional video actually worked
The promotional video showed logins using the onscreen keyboard.
These logins actually worked.
Just more evidence pointing to a total lack of awareness of security.
18. Running anything on an untrusted machine is incredibly dangerous
It’s suggested Wemagin can be used on any machine safely. It’s very, very hard to run anything on an untrusted machine safely.
The host OS can see everything, even if the guest OS is running inside a VM.
On-screen keyboards are not adequate protection against a hostile machine.
There are frequently vulnerabilities that allow data to flow between guest and host OS.
19. A team member has admitted to attempting to smear critics
Team member Paul Lee of Cannysage Studios admitted to making a post on a totally unrelated forum calling me a racist.
Steve Kim has said that you need to trust them. How can you trust a company that acts like this?
20. Clear astroturfing
Paul Lee, a team member, was posting as Paul.
Ruth Read, who says she invested in Wemagin 3.5 years ago, is also posting comments saying she can’t wait to receive the product.
21. The USB stick is off the shelf
“Four separate molds have been made.”
“There are 4 manufacturers on standby.”
But it’s just a off the shelf USB stick from China.
22. Silently altering important details of the project
Notice how some of the claims have gone:
“No digital footprint left on the USB device to track”
“No cache, cookies or history on the computer”
“Masked IP address”
Notice how “no trace” has gone, and “beta” has turned up.
Also, they seem to have got rid of “The Team” on the main Wemagin page. Right after the team member Paul Lee admitted to smearing me.
23. Already tried and failed with WCLOUD
It looks like WCLOUD has been about for a while. Previously, it wasn’t motivated by privacy, secrecy, North Korea or anything like that. It was a lot cheaper.
24. Paying people to promote Wemagin
There are numerous Craigslist job adverts asking for people to promote Wemagin. How many of the people supporting the project are paid?
Conclusion
Would you trust a privacy product that has this many inconsistencies, exaggerations, and problems?
I know I wouldn’t.
Most of these issues could be cleared up by an improved technical specification along with some changes to the claims.
Questions
We have questions for Steve:
- Is this designed to be used inside North Korea, China, Iran, and Syria safely?
- Is Wemagin “low trace” (leaves no trace visible to some with average skills) or “no trace” (leaves no trace even after detailed forensic examination)?
- Is Wemagin re-labelling cloud and VPN services from other providers?
- Your beta testers and security testing have missed some very obvious problems. How are these going to be addressed?
Motivation
Why am I doing this? Shouldn’t a small start-up have every chance to deliver this project?
No.
I am absolutely fine with companies producing tools to help middle-aged white men in Western countries access porn without their spouses knowing.
I am absolutely fine with companies producing tools to help school-kids bypass restrictive firewalls preventing them accessing the Anarchists Cookbook.
I am not absolutely fine with companies producing tools where they claim to be able to protect people in repressive regimes when everything indicates this is going to put them at great risk.
I am not absolutely fine with companies using emotive images like emaciated children in North Korea to make a quick buck.
Wemagin started as a project with outlandish claims but the behaviour of the creator has put it into the territory of outright dishonesty.
I am not a competitor to Wemagin.
I am not being paid to criticise Wemagin.
Nothing I have said here is untrue or unfair. There is a worrying tendency at the moment for people to call any robust, reasonable criticism “bullying“. It isn’t bullying – it’s other people telling you that what you are saying is not adding up. You are free to respond to concerns, free to contact me, free to point out if anything I have said is untrue.
Yet, supporters of Wemagin think it is:
- Acceptable to threaten to disclose my personal address (the user was banned from commenting after this)
- Acceptable to call people “douchebag”
- Acceptable to go through my photos, deface them, and send them to me.
- Bringing up irrelevant Internet history somehow means criticism is unwarranted.
Really, who are the bullies here?
The bullies are Wemagin. All of the image links here are on Imgur to avoid any accusations of tampering.
On Sunday, I saw hits coming from a car forum called NASIOC:
http://i.imgur.com/2aeybl0.png (no link, as private).
I visited the site to find a user, Wardroid, posted a thread entitled “Racist Cyber bully” claiming I had said “jap tech is overrated”:
http://i.imgur.com/yore3k1.png
The thread has since been deleted – because it was against the rules of the forum – but here is the google cache:
http://webcache.googleusercontent.com/search?q=cache:rPxerViwF7EJ:forums.nasioc.com/forums/showthread.php%3Ft%3D2680816
I have no way of proving that I didn’t do something, but most people who know me would say it would be extremely out of character to post something like that. It’s also really the job of the accuser to prove something like that.
The user who started the thread “Wardroid” has posted several videos to youtube as user “canny3d”:
http://i.imgur.com/F1MlVZf.png
http://forums.nasioc.com/forums/showthread.php?t=2649998
https://www.youtube.com/watch?v=2H6YrZif6eY&feature=youtu.be
You’ll note that this video is by “Cannysage Studios”.
http://i.imgur.com/kcH33gy.png
You may recognise this name from wemagin.com where he is listed as a video consultant:
http://i.imgur.com/7cKTH0W.png
When asked about this on twitter, Paul Lee said:
“I got an anonymous email that you were a racist and don’t like asians.”
http://i.imgur.com/0WdLQ9I.png
https://twitter.com/cannysage/status/533904373819002880
So a team member of Wemagin got an anonymous email that I am racist, found absolutely zero evidence of this, went onto a car forum and posted a thread to incite abuse.
Of course, we need to link this to Paul from Kickstarter.
This post of the forum uses a link to my page “Bad companies”, something with the user Paul has taken issue with before:
https://www.kickstarter.com/projects/1052775620/wemagin-smart-usb-drive/comments?cursor=8345552#comment-8345551
It also uses very similar language to Paul’s post:
He’s self-claimed ‘hacker’ and security researcher, lol. viral material in development.
also claiming that you are a ‘hardware hacker,’ LOL.
The forum post was made on the forum very shortly after Paul was banned from commenting on Kickstarter after threatening to disclose my personal address and mentioning that he had gone through my photos (which were then mentioned in the forum post):
http://i.imgur.com/zy1DXsB.png
I have further evidence that Paul Lee of Cannysage Studios is harassing me but it steps across the line of “doxxing” to post it. So I won’t.








Anon
November 14, 2014 at 7:58amHey there, this is a good summary of what’s wrong with this.
Yesterday on 4chan’s technology some anonymous user pointed out that the VPN solution used here is basically white label “IPVanish”, just like with Livedrive, they are just reselling something.
Someone also pointed out that THE LOGINS USED IN THE VIDEOS REALLY WORK.
This product and the people behind it is all very suspicious and it’s clear they don’t know anything about privacy and security.
Here’s the thread if anyone’s interested: https://archive.rebeccablacktech.com/g/thread/S45143318#p45146443
K
November 15, 2014 at 4:04pmYou have my congratulations and my thanks for sticking with this so long–the comments would have driven me mad weeks ago.
I know virtually nothing about the technical questions at issue–just enough to recognize that they’re serious ones that require answering–but there’s also another, non-technical, point that’s been nagging at me: their timeline for August 2014 lists “successful testing of tracking down device if lost or stolen”. Shouldn’t “successful tracking” be a bug, not a feature?
It’s listed in the patent as well, and while I realize the device they sell needn’t be the one they’ve applied for patent on, I’m still not thrilled with “The exemplary embodiment tracks where the USB Flash Drive is, if stolen or lost, and tracks when, where and how often the USB Flash Drive is accessed.” or “If the USB flash drive is registered by the owner as lost or stolen, or if unauthorized access is attempted, the exemplary embodiment tracks the IP address of the device with which the USB flash drive has been connected. Thus, the location of the USB flash drive can be tracked.”
In an excess of fairness I’ll grant that Wemagin doesn’t explicitly claim it’ll hide my physical location while I’m using it, but nonetheless, providing any sort of digital access to my whereabouts isn’t exactly consistent with their relentless focus on privacy. Presumably Steve hopes we’ll just trust him that this “security system” in the patent isn’t included on the Wemagin version, despite what the timeline says.
I can’t quite bring myself to back the project, even temporarily for just long enough to ask this, and more importantly I don’t want to distract the discussion from the pressure you’re putting on Steve, but it seemed like it might be a good example of a question from a non-technical user that Steve should have an answer for. I can’t be accused of not understanding VPNs or cryptography or registries, since I’m not claiming to. It’s just, “hey Steve, I’m confused, how is it the device can be tracked but I can’t?”. It ought, in theory, be hard for him to get out of that one. (Though a guy who claims, on November 11, that his critics stand in the way of “preventing great wars”, is capable of anything.)
Anyway, thanks for your patience & persistence in dealing with all this.
cybergibbons
November 15, 2014 at 4:58pmThanks for the comment.
This aspect of it had passed me by. Yes – another inconsistency. Being able to detect unauthorised use, and then track that use, does go against the “no logging” that is now claimed on the VPN server.
I’ll write this up in the main post. Thanks once again.
K
November 15, 2014 at 6:17pmMuch more succinct–thank you! One final timeline point & I’ll stop flooding your comments: I’d dearly love to know how Steve guarantees his politically disruptive device hasn’t been compromised by its Chinese manufacturers (June 2012; Dec 2013).
K
November 18, 2014 at 12:31amThe cover photo for the campaign has changed. There’s now a ‘beta’ label and the claims “nothing on the computer”/”nothing on the USB device” are now “PC (no traceable internet information)”/”USB device (no traceable internet information)”. Former (archive.org, Nov 10): http://i.imgur.com/C0tEWF5.jpg; current (Nov 17): http://i.imgur.com/r2snmDC.jpg.
cybergibbons
November 21, 2014 at 12:05pmThanks – we’ve also got a load of screenshots. I suspect the moving of the goalposts is happening so we can be called liars.
Wemagin VPN or Support TOR
November 25, 2014 at 10:20pm[…] More detail on Wemagin can be found here : http://cybergibbons.com/security-2/why-does-the-wemagin-internet-privacy-gadget-look-like-snake-oil/ […]
Michael
November 25, 2014 at 10:24pmCybergibbons — Thanks for your response to our tweet and thanks for your deeper investigation to wemagin security/ anonymity product. We only scratched the surface https://vpnreviewz.com/wemagin-vpn-or-support-tor/ compared to your article nonetheless we seemed to have reached a similar. Just use TOR or if you actually need a VPN / smart DNS service look elsewhere. We linked to your article. Thanks for your work online!
Concerned Anon
December 15, 2014 at 10:39amCybergibbons, thank you very much for such a detailed research! In the age of snake-oil sellers,
we need people like you who could help the beginner users to spot the fraudsters (and find a better protection instead)
Just a small question:
Have you reported this project to Kickstarter, with a link to research results – provided in article above?
If not, please do it right now! Just 4 days have passed, and maybe the project’s funding could still be revoked
Charlatans: The new wave of privacy profiteers | iTelNews
December 23, 2014 at 2:23pm[…] certainly one of those skeptical about Wemagin’s incredible claims. His measured examination Wemagin is Wemaginary neatly dissected a whole lot of Wemagin’s problematic claims, in numbered order. Highlights […]
Charlatans: The new wave of privacy profiteers | Proxinator
December 24, 2014 at 12:17pm[…] positively one of those doubtful about Wemagin’s implausible claims. His totalled hearing Wemagin is Wemaginary orderly dissected a whole lot of Wemagin’s cryptic claims, in numbered order. Highlights […]
Charlatans: The new wave of privacy profiteers | TKGNEWS.COM
December 25, 2014 at 7:13am[…] certainly one of those skeptical about Wemagin’s incredible claims. His measured examination Wemagin is Wemaginary neatly dissected a whole lot of Wemagin’s problematic claims, in numbered order. Highlights […]
Jason
February 18, 2015 at 5:29amThanks for your diligent attention to detail, keep fighting the good fight!
Fake privacy gadgets, from Anonabox to Sever: Fighting a strange and profitable epidemic | iTelNews
May 7, 2015 at 11:16am[…] Kickstarter completed at $54,607. It was actually called WEMAGIN PRIVACY GADGET, and debunked publicly. Wemagin still has not […]
Fake privacy gadgets, from Anonabox to Sever: Fighting a strange and … – KnowGadget
May 8, 2015 at 4:57am[…] Kickstarter finished during $54,607. It was indeed called WEMAGIN PRIVACY GADGET, and debunked publicly. Wemagin still has not […]