NeighbourNET (caution, awful Flash splash page) is a platform used to power a number of local community websites in London:
- www.ActonW3.com
- www.BrentfordTW8.com
- www.ChiswickW4.com
- www.EalingToday.co.uk
- www.FulhamSW6.com
- www.HammersmithToday.co.uk
- www.PutneySW15.com
- www.ShepherdsbushW12.com
- www.WandsworthSW18.com
- www.WimbledonSW19.com
It would be fair to say the visual presentation of the sites hints at there being security problems.
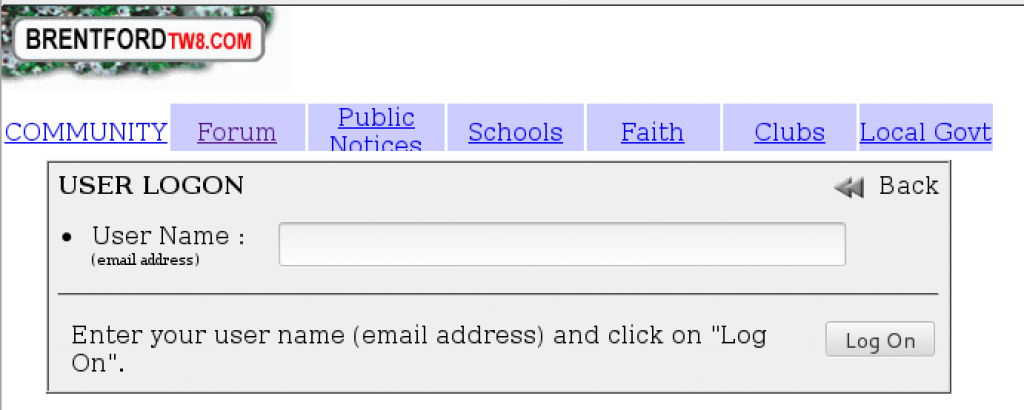
1. No passwords required for login
When you login to the site, all you need is an email address. There are no passwords at all.
2. Posting name can be spoofed
The posting name and email is passed as a parameter when posting a message, and it can be altered to any value you want.

This allows you to post as anyone else on the forum.

3. No cross-site request forgery protection
No requests to the site have any cross-site request forgery protection.
A user can visit another website, and that website can cause them to carry out actions on the site, such as posting messages.
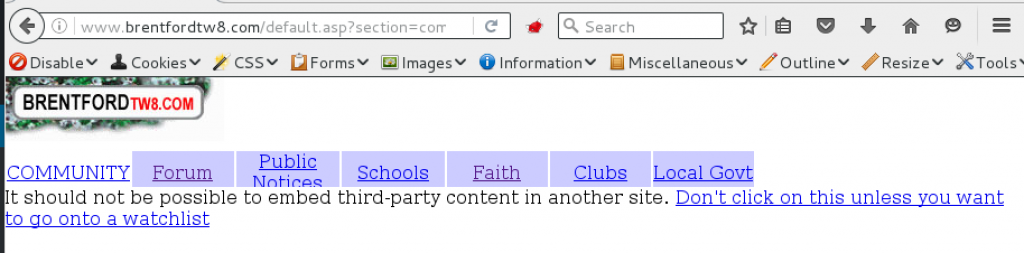
4. Allows embedding of untrusted third-party content
The site embeds it’s own content using a URL passed as a GET parameter.
The source of this content is not whitelisted or validated, so you can just embed your own content. This has only been tested with plain HTML, but if JavaScript, Flash or other content could be embedded, this would lead to cross-site scripting or malware delivery to users.
Conclusion
A mess of security issues. Considering that local councillors use these sites to communicate with the public, allowing impersonation is a serious issue.
Disclosure timeline:
The operators of the sites were informed on 4th May, so after 60 days they are being disclosed.
03/05/2016 – first email sent to NeighbourNET
04/05/2016 – email response received, issues sent by email, receipt acknowledged
17/05/2016 – chase on further response
14/06/2016 – chase on further response and state disclosure date of around 04/07/2016. Email acknowledged.
17/06/2016 – get response from vendor:
Chatted to the development team about the issues you raised.
They acknowledged that you have identified some potential security holes but they have existed for a long time without ever been exploited and there seems little incentive for anyone to try to do so.
We have been for some time now working on completely overhauled site architecture and whilst this project has been ongoing for sometime we are now talking in terms of months rather than years before implementation. This would close these security holes and others.
White hat banned for revealing vulns in news sites used by London councillors (The Register) – sec.uno
July 11, 2016 at 6:32am[…] “It would be fair to say the visual presentation of the sites hints at there being security problems,” Tierney says. […]
Vulnerabilities in London News Websites get White Hat Banned – HOTforSecurity
July 11, 2016 at 11:17am[…] be fair to say the visual presentation of the sites hints at there being security problems,” wrote Tierne. “A mess of security issues. Considering that local councillors use these sites to […]
White hat banned for revealing vulns in news sites used by London councillors | VIPshield.co.uk
July 11, 2016 at 6:31pm[…] “It would be fair to say the visual presentation of the sites hints at there being security problems,” Tierney says. […]
Security analyst banned for disclosing vulnerabilities in forums
July 12, 2016 at 12:38am[…] This is a dangerous security oversight, as Tierney explains in a blog post: […]