NOTE – slashes are getting messed with by WordPress, I am sure you’ll be able to work it out.
We’ve had a quick look at the HEX file, but what about the programming utility we have downloaded? This is to program the NVM (Non-Volatile Memory), which is a socketed EEPROM on the board. This is a quite common mechanism for storing and modifying settings in security equipment.
CS0054_setup.msi is a Windows installer that installs a series of applications in C:Program Files (x86)CSL. There are the following applications:
- CS0054 Universal Programmer
- CS1054 Programmer for Dualcom Plus
- CS2054 Programmer for Dualcom GSM
- CS2364 Programmer for Dualcom GRPS
Let’s start with CS2364 – the programmer for the DualCom GPRS. The others are older communicators that we don’t have. We might come back to the other utilities later.
When you start this program up, you are presented with a fairly blank screen:

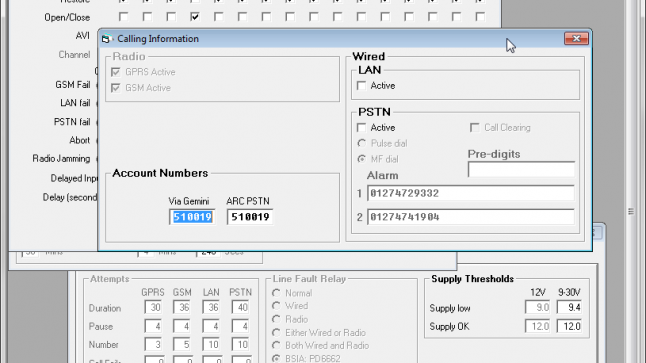
And there a number of dialogs accessible, allowing us to set some obvious and not so obvious options:



The top most dialog required setting the option “System” in the options dialog. There are also a lot of greyed out options. How do we get them enabled?
The program looks like it is pretty old – VB, probably no notion of Internet connectivity. The settings are likely to be stored in a file or the registry.
Let’s use Process Monitor to… monitor the process. This is a Microsoft utility that shows file and registry activities for running programs. It can often hint at where a program is looking for settings and license keys.
You filter the output down to show the process and actions you want to see, or you will be overwhelmed by other application’s data.
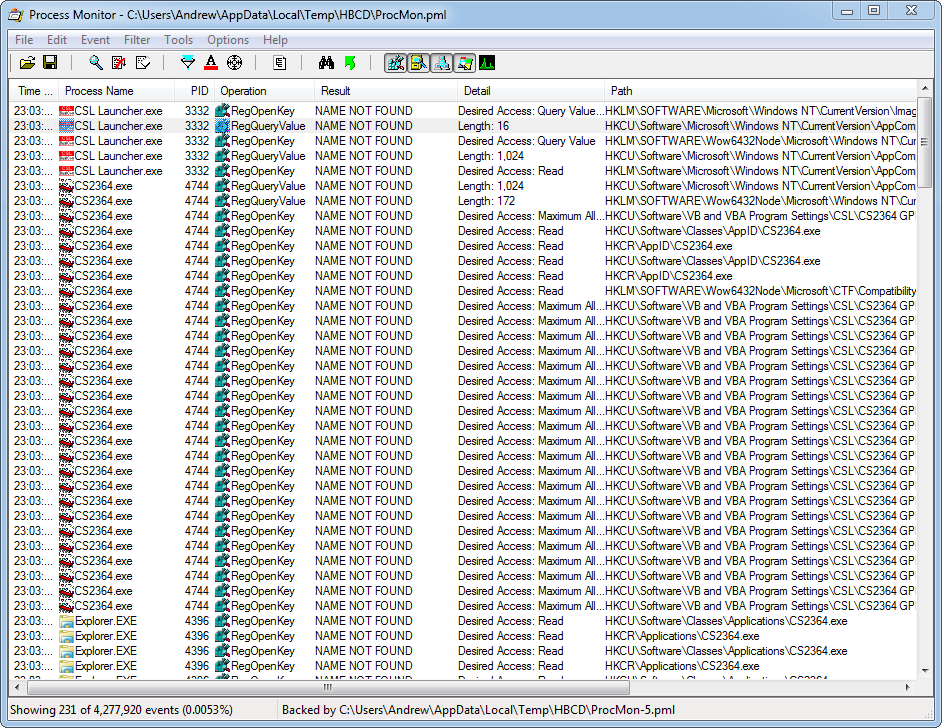
We can see that the program accesses the following registry key:
HKCU\Software\VB and VBA Program Settings\CSL\CS2364 GPRS DualCom\Options\System
and reads a value of “True” from REG_SZ key:
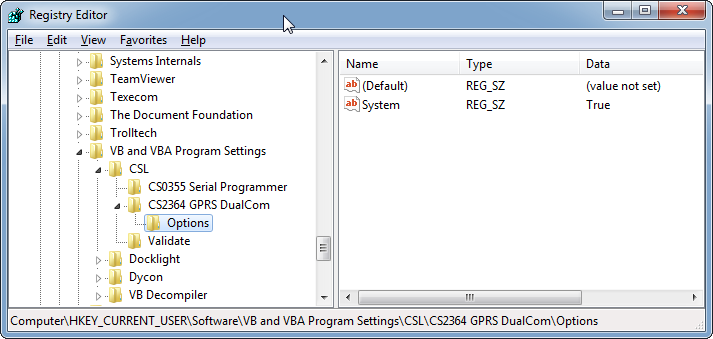
If I turn off “System” in the options dialog, I see this value get set to “False”. This is good – the settings are stored very simply in the registry. So where else is the program looking?
HKCU\Software\VB and VBA Program Settings\CSL\CS2364 GPRS DualCom\Options\Factory
HKCU\Software\VB and VBA Program Settings\CSL\CS2364 GPRS DualCom\Options\Numbers
HKCU\Software\VB and VBA Program Settings\CSL\CS2364 GPRS DualCom\Options\Jamming
HKCU\Software\VB and VBA Program Settings\CSL\CS2364 GPRS DualCom\Options\Mon&Outputs
I can’t see any options in the front-end for these. Let’s create values and set them to “True”, one by one, and see what happens.
Factory
When we startup now, we get an error dialog:
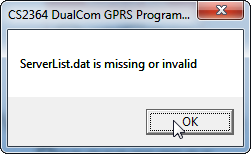
There isn’t a file present called ServerList.dat – so it must be missing rather than malformed. .dat files are very often binary, so it can be hard to work out what should be in them. Disassembly is often the way forwards, but it’s not of importance at the moment.
Once in the program, we now have some additional options. Under View, we now have LAN:

Under NVM we now have Program (which just complains about the programmer not being present, as we have no programmer). It’s odd that without this setting, we can Read and Compare the EEPROM, but not
We also have a new option in the System dialog which says “NVM Config Requires Update”. I can’t see any other differences in the UI.
Numbers, Jamming, Mon&Outputs
I can’t see any difference with these set to True, or when I try various combinations of True/False.
So we seem to have the program in some kind of factory mode. All of the values are blank or 0 though. However, if we go to File, Open, we find Sample.prm. Open this file, and now the dialogs show numbers and settings. This must be an example for programming the EEPROM. Still a lot of
Opening the Sample.prm file in a text-editor, I can see that it is a text file, with the following format:
H,47,00
25
00
00
00
2F
00
00
00
00
00
00
00
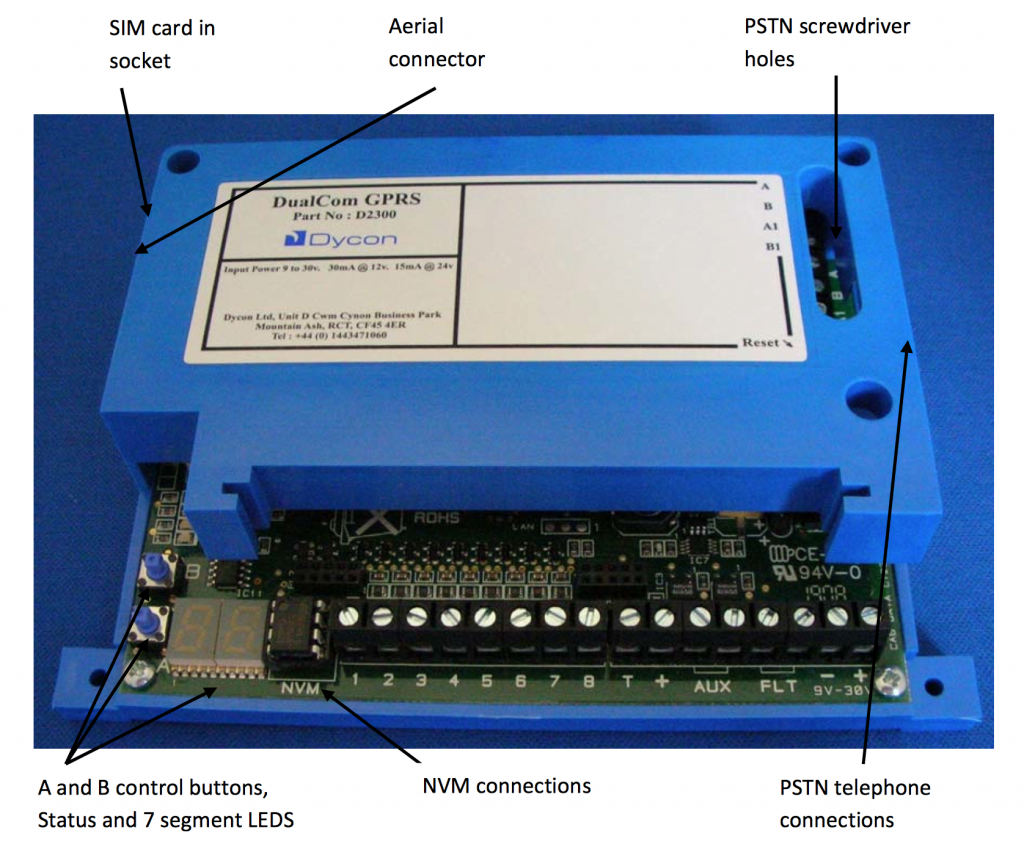
If we look to the board, the socketed EEPROM is a 93C86 – which is a 2048x8bit EEPROM. It’s quite likely that this file represents the contents of that EEPROM with some overhead – maybe the Site Details are stored in the file but not the EEPROM.
I can see in the program that the SIM ICCID is as follows:

This is a long, unique number. We should be able to find this in the Sample.prm file:

There it is – stored as a number in 304-313.
Whilst looking at the file, I noticed a lot of values in the range 30-39. These are ASCII for 0-9 i.e. these could be numbers and text represented in ASCII instead of raw number as with the ICCID.
A quick python program to convert the ASCII range values into strings:
datafile = open('f:\data\Sample.prm','r')
combstr = ''
for row in datafile:
# Just rows with a two character entry
if len(row) == 3:
# Ignore > 127 which are not simple ASCII
if int(row,16) < 128:
# Put a space for 0 to show breaks
if (int(row,16) == 0):
combstr = combstr + ' '
else:
combstr = combstr + chr(int(row,16))
outfile = open('f:\data\Sample.prm_string.txt', 'w')
outfile.write(combstr)
outfile.close()
The output of this can be downloaded here.
And now we can see that there are quite a few strings in the Sample.prm:
01895460023 // Phone number - as a string as likely it is sent via AT commands
172.168.10.10:9000 // IP address and port
apn6.com // Details including username and pass for an APN?
csldual.comv
dualcomgprs19
QO680677
Also, interestingly, the filename “Sample.prm” is stored in the file itself towards the end. This is probably the overhead that makes the prm file bigger than 2048 lines.
When exiting the program, it stores a new file – last.prm – which includes any changes you have made. There is no Save. Interestingly, when running this through the Python script above – I see the following:
CS2364:X220:Andrew
So that’s my hostname and login name for the machine stored in the overhead at the end. Interesting!